IdentityIQ presents a holistic approach to identity management, providing a range of tools specifically crafted to assist organizations in efficiently handling user identities, access privileges, and security policies.
By offering a centralized platform, it enables the automation and streamlining of identity governance and administration (IGA) processes. But don’t know why people are asking, “Is IdentityIQ legit or not?”
IdentityIQ by SailPoint offers a streamlined solution for identity governance, efficiently managing user access and ensuring compliance with policies like GDPR, HIPAA, and SOX.
It automates key identity management tasks, which raises the question: Is IdentityIQ legit in its support for seamless integration with diverse IT environments?
With a user-friendly interface and advanced analytics, IdentityIQ is ideal for medium to large-sized organizations prioritizing secure, efficient identity management.
Table of Contents
Is IdentityIQ Legit? Step-by-Step Guide to Assessing Legitimacy
Assessing the legitimacy of a software solution like IdentityIQ involves a series of steps that help verify its authenticity, security, and reliability.
Here’s a step-by-step guide to help you evaluate is IdentityIQ legit:
- Research the Provider (SailPoint):
- Look into SailPoint’s history, market reputation, and track record in the identity governance space.
- Check for any major security incidents or breaches associated with SailPoint.
- Examine Product Certifications and Compliance:
- Verify if IdentityIQ complies with relevant industry standards and regulations (like GDPR, HIPAA, or SOX).
- Look for certifications (e.g., ISO 27001) that demonstrate adherence to security and quality standards.
- Explore Customer Reviews and Case Studies:
- Read customer testimonials and case studies to understand real-world applications and satisfaction levels.
- Look for reviews on independent software review platforms or IT forums.
- Assess Product Features and Capabilities:
- Evaluate IdentityIQ’s features against your organization’s specific needs for identity governance.
- Consider the software’s scalability, integration capabilities, and user-friendliness.
- Inquire About Support and Maintenance:
- Understand the type of customer support provided, including availability and responsiveness.
- Check the frequency and quality of software updates and maintenance releases.
- Request a Demo or Trial:
- A hands-on experience through a demo or trial period can give you a practical understanding of the software.
- Use this opportunity to ask specific questions and gauge the software’s performance.
- Consult with IT Security Experts:
- Engage with IT security consultants or industry experts to get an unbiased opinion about the software.
- Discuss any potential security concerns or compatibility issues.
- Analyze Cost-Benefit:
- Consider the pricing of IdentityIQ in relation to the features and benefits it offers.
- Weigh the cost against the potential ROI in terms of improved security and efficiency.
- Check for Integration Compatibility:
- Ensure that IdentityIQ is compatible with your existing IT infrastructure and systems.
- Look for any potential integration challenges that might arise.
- Review Security Protocols:
- Investigate the security measures and protocols IdentityIQ uses to protect data.
- Understand how the software will contribute to your organization’s overall cybersecurity posture.
- Understand the Terms of Agreement:
- Carefully read the terms and conditions, focusing on data usage, privacy policies, and service level agreements (SLAs).
- Seek Peer Insights:
- Reach out to peers in your industry who might have used or are currently using IdentityIQ.
- Gain insights from their experiences and best practices.
By adhering to these procedures, you can ensure a comprehensive evaluation of, is IdentityIQ legit and suitability in meeting your organization’s identity governance needs.
Hidden IdentityIQ Features You Didn’t Know About
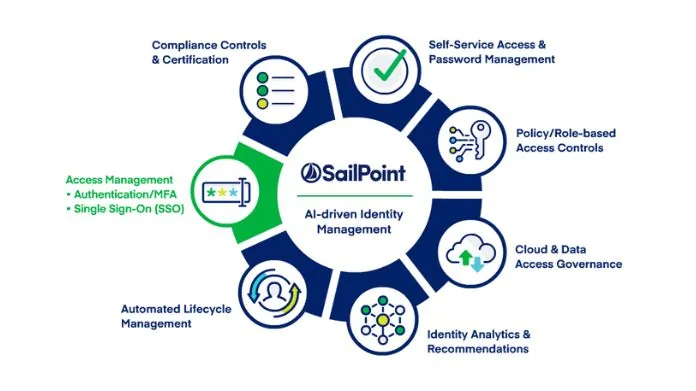 SailPoint’s IdentityIQ is widely recognized for its all-encompassing set of identity governance and administration features.
SailPoint’s IdentityIQ is widely recognized for its all-encompassing set of identity governance and administration features.
Nonetheless, there are various lesser-known or underutilized functionalities that possess the ability to improve your identity management strategy substantially.
- Advanced Analytics and AI Integration: IdentityIQ offers advanced analytics capabilities that can predict potential risks and anomalies in user access. Integration with AI technologies further enhances this, allowing for smarter decision-making and proactive governance.
- Customizable Dashboards and Reporting: Beyond standard reporting features, IdentityIQ allows for highly customizable dashboards. Users can tailor these dashboards to display specific metrics or data points relevant to their unique role or governance needs.
- Robust Policy Simulation and Testing: Before implementing new access policies, IdentityIQ can simulate their impact. This helps in understanding the potential effects of policy changes without risking actual system changes.
- Access Request Recommendations: Utilizing machine learning, IdentityIQ can provide intelligent recommendations for access requests. This feature helps streamline the approval process and reduces the risk of inappropriate access being granted.
- Context-Aware Security: IdentityIQ can adjust security requirements based on contextual data, such as user location, device type, or time of access.
- Comprehensive Identity Warehousing: The platform offers a robust identity data warehouse feature, which enables long-term storage, reporting, and analysis of identity-related data. This can be crucial for compliance and historical analysis.
- Automated Risk Scoring: IdentityIQ can automatically assign risk scores to different users or access rights, helping prioritize governance efforts where they are most needed.
- Integration with Third-Party Applications: While its ability to integrate with a wide range of applications is known, the depth and flexibility of these integrations can be underexplored. IdentityIQ can work in tandem with an array of third-party security and IT management tools.
- Mobile Device Management (MDM) Integration: IdentityIQ can integrate with MDM solutions to extend identity governance capabilities to mobile devices, ensuring comprehensive coverage across all user endpoints.
- Self-Service Access Requests with Automated Fulfillment: The self-service portal is often underutilized. It allows users to request access to resources autonomously, while automated fulfillment capabilities can speed up the provisioning process.
- Delegated Administration for Decentralized Management: This feature allows the delegation of certain administrative tasks to non-admin users, which can be especially useful for distributing the workload in large organizations.
- Behavioral Analytics: IdentityIQ can track and analyze user behavior patterns, offering insights that can be used to refine access policies and detect potential security threats.
The Upside of IdentityIQ: Exploring the Pros and Perks
IdentityIQ offers a comprehensive set of features and functionalities that enable organizations to manage and govern user identities effectively.
This includes capabilities such as user provisioning, access certification, and role management, among others.
- Comprehensive Identity Governance: IdentityIQ provides a holistic approach to managing user identities, access permissions, and security policies. This comprehensive coverage is essential for organizations with complex IT environments, ensuring that all aspects of identity and access management are properly governed.
- Improved Security and Compliance: The platform significantly enhances an organization’s security posture by reducing the risk of unauthorized access. It ensures compliance with various regulatory standards (like GDPR, HIPAA, and SOX) through robust policy enforcement, audit trails, and reporting capabilities.
- Automated User Lifecycle Management: IdentityIQ automates critical processes involved in user lifecycle management, from onboarding to offboarding. This automation not only saves time but also minimizes the risk of human error, ensuring that access rights are accurately assigned and revoked in a timely manner.
- Role-based Access Control: The solution simplifies the management of user access by utilizing role-based access controls (RBAC). This approach streamlines the assignment of access rights, making it easier to manage permissions based on user roles within the organization.
- Scalability and Flexibility: IdentityIQ is designed to scale with the growth of an organization. It can handle the increasing number of users and complexities in IT environments, providing flexibility in accommodating new technologies and business changes.
- User-friendly Interface: The platform offers an intuitive interface, making it accessible for both administrators and end-users. This ease of use enhances user adoption and reduces the learning curve associated with new software implementations.
- Advanced Analytics and Reporting: With its advanced analytics and reporting tools, IdentityIQ provides valuable insights into access patterns, potential security risks, and operational efficiency. These insights aid in informed decision-making and proactive risk management.
- Integration Capabilities: IdentityIQ can seamlessly integrate with a wide range of IT systems and applications, both on-premises and in the cloud. This integration capability ensures that identity management is consistent across the entire IT ecosystem.
- Self-service Features: The self-service portal empowers users to manage certain aspects of their identity and access rights, such as password resets and access requests. This feature reduces the administrative burden on IT staff and improves user satisfaction.
- Consistent Policy Enforcement: The platform ensures consistent enforcement of security policies across all users and applications, reducing the risk of policy violations and enhancing overall governance.
Frequently Asked Questions
Q. What is IdentityIQ, and Who Develops It?
Ans. IdentityIQ is an identity governance solution developed by SailPoint Technologies, Inc. It offers a comprehensive platform for managing digital identities, access privileges, and security policies within an organization.
Q. How Can I Verify That, is IdentityIQ Legit Software?
Ans. You can identify “Is IdentityIQ legit” by researching SailPoint, the provider, checking their industry reputation, looking for certifications and compliance with standards, reading customer reviews, and examining case studies.
Q. Is Sailpoint a Reputable Company in the Identity Governance Space?
Ans. Yes, SailPoint is widely recognized as a reputable company in the identity governance and administration market. They have a history of providing solutions to a variety of industries and maintaining high standards for security and compliance.
Q. Does IdentityIQ Comply With International Security Standards?
Ans. IdentityIQ typically complies with various international security standards and regulations. However, specific compliance details can vary, so it’s recommended to check the latest compliance information directly from SailPoint or through their product documentation.
Q. Can IdentityIQ Integrate With My Existing It Infrastructure?
Ans. IdentityIQ is known for its strong integration capabilities with a wide range of IT systems and applications, both on-premises and cloud-based. However, it’s essential to assess specific integration needs and capabilities for your unique IT environment.
Q. What Kind of Customer Support Does Sailpoint Offer for IdentityIQ?
Ans. SailPoint offers various levels of customer support for IdentityIQ, including technical support, maintenance updates, and professional services. The specifics can depend on the service agreement with the company.
Q. Is There a Trial Version of IdentityIQ Available?
Ans. The availability of a trial version of IdentityIQ can vary. It’s best to contact SailPoint directly or visit their website for the most current information on trial offerings.
Q. How Does IdentityIQ Ensure the Security of User Data?
Ans. IdentityIQ employs multiple security measures to protect user data, including encryption, role-based access control, regular security audits, and compliance with data protection regulations.
Q. Are There Any Case Studies of Companies Successfully Using IdentityIQ?
Ans. Yes, there are numerous case studies available that showcase how different companies have successfully implemented IdentityIQ. These can typically be found on SailPoint’s website or through a direct inquiry to their sales team.
Q. What is the Cost of Implementing IdentityIQ in an Organization?
Ans. The cost of implementing IdentityIQ varies depending on the size of the organization, the complexity of its IT environment, and the specific features and services required. SailPoint offers customized pricing based on these factors.
Summing Up!
IdentityIQ, developed by SailPoint, has earned a solid reputation in identity governance and administration. This robust solution from an industry leader effectively addresses a range of identity and access management challenges.
Its credibility is backed by international security standards compliance, positive customer feedback, reliable performance, and seamless IT infrastructure integration.
SailPoint’s transparency about IdentityIQ’s capabilities, coupled with excellent customer support and detailed case studies, enhances its trustworthiness. Moreover, its customizable and scalable architecture suits organizations of various sizes and needs.





